Introducing the Tresorit tools empowering IT admins

The vital work of IT administrators forms the heart of an organization’s digital defenses.
But to truly tackle the challenges of cybersecurity, IT professionals need to be empowered with the right tools for the job: whether that’s permission controls based on the needs of individual projects, clearer metrics, or easy device management.
At Tresorit, we design our end-to-end encrypted products in adherence to strict zero-knowledge principles. But we also prioritize features that give IT admins precise and efficient control over user and file activities.
In this article, we’ll be talking through some of our key admin offerings, as well as talking to existing Tresorit customers about how each solution works in everyday offices across the globe.
User management made simple
Tresorit’s admin center dashboard gives an overview of what’s happening in the company’s account and makes it easy for administrators to manage users.
It’s where organizations begin their Tresorit journey with the onboarding of employees.
Admins can invite individual users to join Tresorit via email or use our domain management tool to claim ownership of a domain, automatically enrolling employees in the organization’s Tresorit subscription.
Users can then be divided into different groups and assigned policies or permissions en masse. This allows administrators to ensure that end users do not violate internal data security rules while also making it easier for them to comply with those rules.
User groups can also be assigned different data residency choices to fulfill regional compliance requirements. Tresorit provides 12 data residency options: Brazil, Canada, France, Germany, Ireland, the Netherlands, Singapore, Switzerland, UAE, UK, and two US locations.
These tools give Tresorit customers such as Trade Republic the confidence to share and store sensitive files with Tresorit, safe in the knowledge they can enforce least privilege principles.
The company uses Tresorit to store all documents that require additional data protection — from personal data and financial data to customer complaints.
“When we need to have this extra layer of security when it comes to certain topics and handling personal data, we do it with Tresorit,” says Raza Perez, the company‘s strategic operations lead.
Help is also in place for admins looking to offboard users. Tresorit’s remote wipe function can remove data from user devices directly from the admin center, mitigating the risk of data leakage if company hardware isn’t returned by departing employees. Individual devices can also have their access to Tresorit revoked outright, which can also help organizations if a device is lost or stolen.
Meanwhile, the folder takeover feature allows admins to transfer ownership of a user’s folders — meaning that your company’s data never strays out of your complete control.
Control over user and file activity via policies and reports
Good security has to be consistent. Once employees have been onboarded, the Tresorit admit center becomes a hub from which IT admins can monitor ongoing activity.
With Tresorit, admins can tailor general policies, effectively controlling how users interact with data. Policies might include limiting local synchronization, to stop data from finding its way to users’ personal devices, only allowing the creation of encrypted folders, or disabling permanent deletion for company files.
To better safeguard business-critical documents, admins can set up limitations for selected user groups and define which operating systems or mobile platforms they can use to access Tresorit.
These background operations enable IT teams to maintain tight control over data distribution without affecting the primary user interface. For companies like Tresorit client NotCo, an AI-powered food tech company, it allows employees to work with documents quickly and efficiently, while mitigating the risk that sensitive R&D files could fall into the wrong hands.
”We needed a solution that would let us store, upload, edit, re-upload, and share business-critical information quickly, every day, without ever compromising on security. Tresorit strikes the perfect balance,” scientist Julia Berning told Tresorit. “What’s more, files are no longer getting lost on people’s local hard drives.”
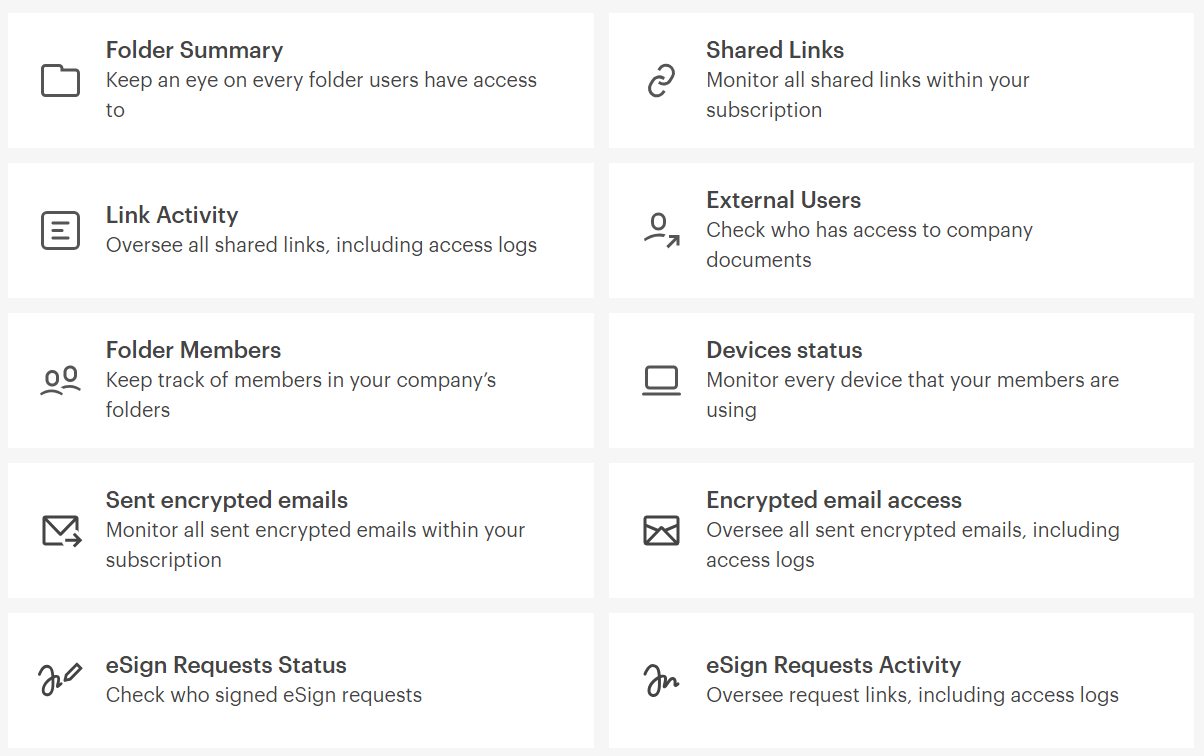
The admin center also gives IT teams an easy overview of the most important statistics on user activities (and integrates with SIEM tools such as Microsoft Sentinel if needed.)
Different reports can also provide a variety of data sets — including lists of all shared links and files, information on who has accessed shared content, and details on from where and when documents have been accessed.
Secure external collaboration
Of course, data security shouldn’t concern you only when thinking about company data managed internally. How can companies stay in control of their data once it leaves the organization’s infrastructure?
Modern businesses need to work alongside global partners within wider supply chains. But sharing information with outside parties also opens a whole range of new security risks. You might trust in your own company’s cyber defenses — but what about your suppliers’?
Tresorit believes that better collaboration shouldn’t have to sacrifice cybersecurity. When companies share or store a file inside Tresorit’s workspace, they receive all the benefits of our industry-leading end-to-end encryption. It ensures that no one but your intended recipient can read your files — not even Tresorit itself.
Once secured, these documents can then be distributed to outside parties using sharing links, providing a safer alternative to email attachments.
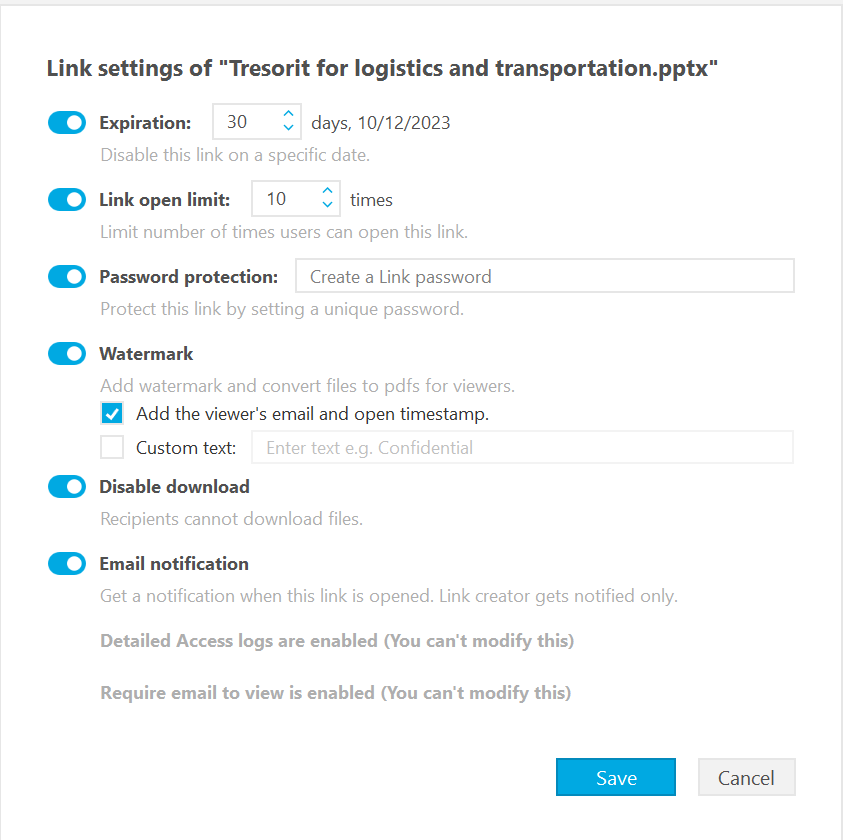
IT admins can customize branding for the platform and the shared link download pages to reflect their brand and enhance trust. With our latest feature, they can also set up a domain and customize the URLs of shared links: an extra reassurance for similarly security-minded business partners who may receive your files. The new format also helps sharing links contend with firewalls, and is designed to add a professional touch to your business’ online activities.
Shared links can also carry additional security measures, such as password protection, expiry dates or link open limits. They also offer customizable watermarks for your documents, or the right to simply revoke user access outright if needed — meaning that even data is being shared outside your infrastructure, it isn’t being shared outside of your control. Furthermore, it's possible to disable downloads, allowing recipients to only view the shared document.
Manufacturing group Viessmann used Tresorit to create clear access rights and responsibilities that govern their data exchanges with third-party suppliers ¬— particularly when handling sensitive R&D files.
“Understandably, our R&D and procurement departments had become extremely cautious when it came to collaborating with external partners, suppliers, and internal colleagues,” says Felix Nolte, Solution Manager for Workspace at Viessmann’s IT Service.
“Since the introduction of Tresorit, our confidential documents are only exchanged through Tresorit – and things have become secure, more controlled, and run smoother for all parties involved.”
But collaboration doesn’t just mean sending files to external partners — it also means receiving documents. Tresorit’s file request function puts power back into the hands of IT administrators. Outside parties can use links to upload documents directly into a secure, dedicated folder. Recipients can view files before accepting them and uploading documents directly into the Tresorit cloud.
You’ve heard from us and our customers — but are you still unsure whether Tresorit could work for you? Our team is on hand to answer any questions you may have, from the finer points of key rotation to system and usability basics.
Alternatively, get your hands on Tresorit and test our IT admin tools for yourself, with our free trial.
Stay tuned for part 2, featuring benefits for end users.






